7 steps to protect your data from ransomware cyber attack

In 2017, the world has encountered several big cyber attacks caused by ransomware, malware that locks up access to computer files and threatens to destroy data if money is not paid. To protect your information from possible blocking or destruction, it is important to understand how this malicious software gets into your computer and what you can do to prevent data loss.
How global community met WannaCry and Petya ransomware
In February-May, WannaCry and its variations attacked and blocked more than 230,000 Windows OS computers around the world, encrypting all data that the hard disk contained. This ransomware blocked files on computers of multinational enterprises, governmental agencies and infrastructure providers. WannaCry caused a serious harm to computer systems in more than 150 countries, including Ukraine, Great Britain, Russia, China, Spain, Italy and Germany.
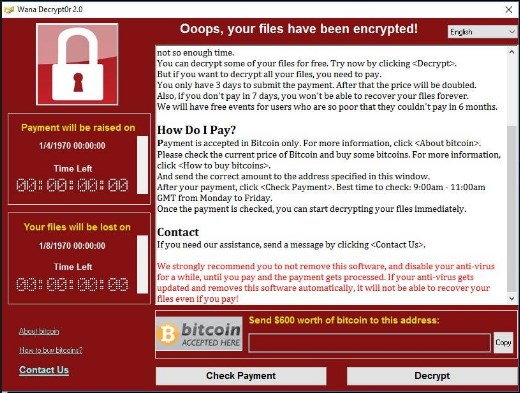
In June, we faced yet another globe-spanning ransomware assault that came from Petya. Unlike WannaCry, Petya spreads internally through networks. This new virus has massively hit Ukraine’s largest enterprises, bank and airport systems and governmental institutions. Victims were also reported in Europe and the U.S.
Most cases of operational system attacks caused by Petya have been provoked by openings of infected documents coming in the format of Word and PDF files. Such documents were sent to emails of many commercial and governmental agencies in Ukraine.
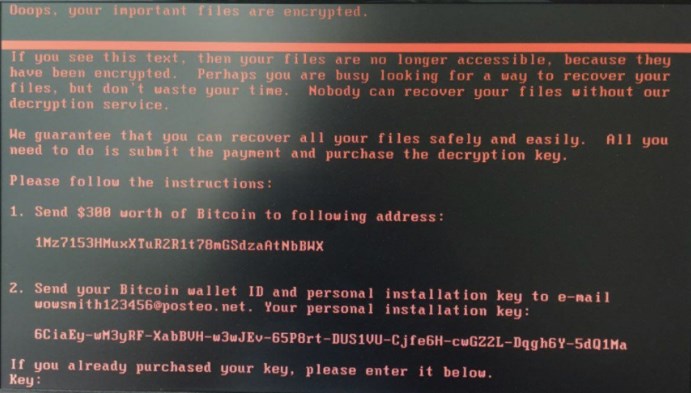
How does Petya work?
Once a computer catches the virus, the ransomware starts traveling rapidly along an organization’s computers, using the network’s MS17-010 vulnerability. The use of this vulnerability results in installing a set of scripts on a computer.
The virus of Petya attacks Windows OS computers by encrypting a user’s files. Then a user sees a warning about file destruction if no ransom is paid in Bitcoins (around $300 to receive a decrypting key that unblocks files).
Symantec confirmed that Petya exploits Eternal Blue, a digital weapon that leaked in April 2017 and is believed to have been created by the U.S. National Security Agency. To protect computer systems from possible attacks, Microsoft released a patch for Eternal Blue (MS17-010), but many businesses have not installed it and were attacked by WannaCry in May.

It is still possible to prevent loss of information caused by a ransomware if you follow seven simple steps when you’re surfing the Internet, checking your emails or working.
1. If your computer has been on and runs normally, but you suspect that it might have been infected, do not restart your computer. Also, if you know for sure that your computer has been affected, don’t restart it. The encrypting virus will start working only after you do a restart and then it will encrypt all files that you store on your computer.
2. Save all your files or at least those that are most important to you from your computer to a hard drive. The perfect solution is to make a backup of all files together with the operational system.
3. To identify the file encryptor on your computer, complete all local tasks and check if you have the following file: C:\Windows\perfc.dat
4. Depending on Windows version you have on your computer, install one of the following ransomware patches released by Microsoft:
-
-
Windows Vista 32 bit – http://download.windowsupdate.com/…/windows6.0-kb4012598-x8…
-
-
-
Windows Vista 64 bit – http://download.windowsupdate.com/…/windows6.0-kb4012598-x6…
-
-
-
Windows 7 32 bit – http://download.windowsupdate.com/…/windows6.1-kb4012212-x8…
-
-
-
Windows 7 64 bit – http://download.windowsupdate.com/…/windows6.1-kb4012212-x6…
-
-
-
Windows 8 32 bit – http://download.windowsupdate.com/…/windows8-rt-kb4012598-x…
-
-
-
Windows 8 64 bit – http://download.windowsupdate.com/…/windows8-rt-kb4012598-x…
-
-
-
Windows 10 32 bit – http://download.windowsupdate.com/…/windows10.0-kb4012606-x…
-
-
Windows 10 64 bit – http://download.windowsupdate.com/…/windows10.0-kb4012606-x…
You can also find the list of patches for less popular and server versions of Windows OS on the website of Microsoft:
https://technet.microsoft.com/…/libr…/security/ms17-010.aspx
5. Make sure you have antivirus software installed on all computer systems and it functions properly and uses the current virus signature database. If necessary, install or update your antivirus software.
6. To reduce the risk of infection, pay close attention to your emails. Do not download or open any files sent from email addresses that are unknown to you. In case you received an email from a known email address, but the content raises concerns, contact the sender and confirm the fact of sending you an email.
7. Do backup of all critical data. Talk to your employees and make sure all of them have the patch installed on their computers and they are familiar with the protection instruction from ransomware. Don’t let any of your staff members work on a computer that doesn’t have one of the patches listed above installed (it doesn’t matter if their computer is connected to a local or global network).
By sharing these recommendations with all of your colleagues, you protect your computer from potential ransomware attack.
Content created by our partner, Onix-systems.
 Home
Home