The Importance of Data Security in Healthcare Software

The role of innovation in the health industry has been continually growing over the last decade. According to a recent report by McKinsey, med-tech’s leading trends include integrated solutions, regulations, smarter devices, and real-time analytics. New software is improving the quality of medical treatment, providing solutions for various issues in healthcare, and enhancing the entire industry’s performance.
However, these improvements come at a price. Security issues caused by various factors can lead to the protected health information (PHI) being compromised, and even the loss of data.
The health industry experiences more breaches than any other sector. Stolen patient records can be sold for $363 per record on the black market. Criminals can use the information for frauds and scams or simply to blackmail individuals, using sensitive information about their physical or mental health. Every data breach reinforces the governments’, healthcare providers’, and patients’ concerns about information security in healthcare.
This article aims to explain the general requirements for data security in healthcare applications and describe the ways to meet those requirements.
The Basics of Healthcare Data Security
First of all, what is protected health information exactly? It is defined as any patient’s information about the identity, medical history, laboratory results, insurance coverage, and other data that can be linked to a specific individual. Its disclosure can cause harm to its owner and penalties for an institution or business that failed to ensure its privacy.
It’s fair to mention that not all healthcare apps are the subject of data protection regulation in different countries. This can be easily defined by checking the functions your app will perform.
If you are going to launch a healthcare education, medical reference, fitness or yoga app, some treatment reminders, or other solutions that don’t require entering, processing, or exchanging very specific user data, you don’t need to worry about those regulations.
However, regional and international regulations should definitely apply if the software you created qualifies as:
- Healthcare reference & database apps
- Professional networking apps
- Doctor appointment & clinical assistance apps
- Patient tracking apps
- Telehealth mobile apps (doctor-on-demand apps)
All these apps deal with different types of personal healthcare information that has to be stored, transmitted, or analyzed by various institutions and strongly protected from third-party intervention.
Healthcare Information Protection in Different Countries
Different countries have their own requirements for protecting this kind of data. So it is important to determine the major regulations that apply to the type of software you develop and major points to pay attention to.
Here are the main healthcare data security regulations you need to follow while developing your own healthcare app:

HIPAA Regulations in the U.S. and Canada
The Health Insurance Portability and Accountability Act, or HIPAA, is the official document that takes under control the individual health information protection. Written in 1996, it is still applicable for various software utilized in the medical industry, such as email providers and Internet platforms, cloud services, and other digital resources where any personal information about the health status of patients is applied, transferred, or exchanged.
The main principles of these regulations are as follows
- Content encryption: Any electronic protected health information (ePHI) must be encrypted before the transmission.
- Storage encryption: The electronic patient PHI storage must be encrypted.
- Backup adapting: The data has to be recovered and restored if needed.
- Data access: Any ePHI is available for the authorized staff.
- Data integrity: The ePHI can’t be changed illegally.
- Secure disposal: The ePHI will be removed from the storage permanently if it is no longer needed.
- Business Associate Agreement: The most critical point is that the ePHI can be hosted only on services that have signed the Business Associate Agreement. If not, the data should be hosted on secure in-house servers.
PIPEDA in Canada
In 2000, Canada published an equivalent regulation – the Personal Information Protection and Electronic Documents Act (PIPEDA). The protected health information includes the general patient’s information like name/surname, personal ID, credit information, and medical records.
GDPR Regulations in Europe
If you are targeting the international market, it is important to comply with the requirements of the United Kingdom and European Union known as the General Data Protection Regulations. GDPR was adopted in 2018 to regulate data exchange between the EU members and promote the safety of each EU resident’s electronic personal healthcare information.
Non-EU countries, such as Serbia, Norway, or Iceland, have also accepted the GDPR or adjusted them for their respective healthcare sectors.
This system covers a broad range of software and has more general regulations than HIPAA’s. To get approval for a healthcare app in Europe, you should follow these regulations:
- Inform your clients. All the information about the data storage and transmission should be delivered to the users.
- Provide the reasons for data exchange.
- Get approval from the data owner.
- Anonymize the data collected.
- Provide access to the data owners.
- Notify the data owners about any breaches.
- Allow the data owners to withdraw their consent of personal data processing.
- Ensure secure data flow and exchange.
- Delete personal information upon request.
International Standards of Asia-Pacific Region
The medical information in this region is regulated by different laws, which are rather close to the GDPR but include each region’s regulatory requirements, enforcement, and export regulations.
Here is a list of countries and their personal health data rules, sorted by the level of regulation, starting from the highest:
- China – CyberSecurity Law
- South Korea – Personal Information Protection Act
- Taiwan – Personal Data Protection Act
- India – Digital Information Security in Healthcare Act
- Australia – Privacy Act
There are many things to consider to comply with the HIPAA regulations in the US, PIPEDA in Canada, GDPR in the EU, and so forth, before launching your own software in the healthcare market. Of course, once built, the app should be improved on a regular basis to prevent third-party intervention.
According to the HIPAA Journal, 4,467,098 healthcare records were reported as breached in January 2021. This number exceeded the total of December 2020 by more than 225,000 records and was four times as many as in November. It’s even more shocking when we learn that January actually saw fewer attacks than the previous month.
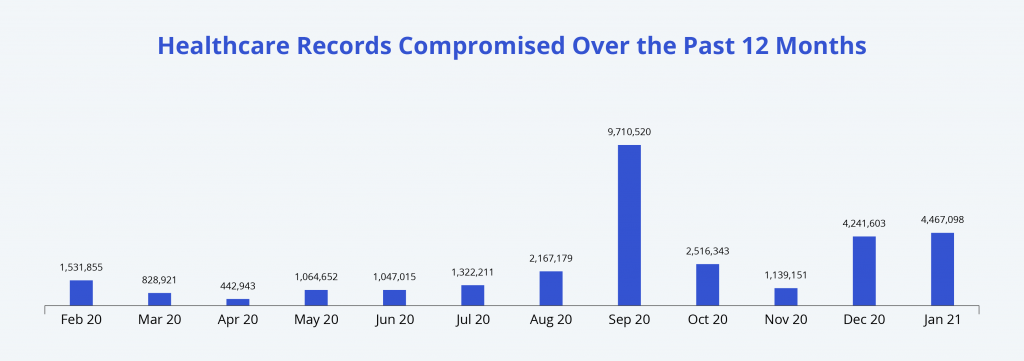
Because these attacks are becoming more extensive, they can result in much higher losses for the companies.
What are the weakest points that hackers target and that may cause data breaches? Here is a short list of the critical factors to consider.
#1 Use of Outdated Software, Legacy Systems, and Obsolete Technologies
The implementation of electronic health records (EHR) has increased both the quality of the healthcare institutions’ performance and the risk of being attacked. If they are using out-dated software and hardware, it becomes much easier for criminals to steal the patients’ data.
#2 Cloud Threats
As the patients’ data grows faster and faster, storing it effectively and securely becomes a priority. More and more medical apps utilize cloud storage for their data flow. However, cloud computing systems can also be a weak point that criminals can exploit. As a result, the health information including all the names, numbers, and records may end up in the hands of third parties, causing a huge loss of trust and investments.
#3 Transfer of Electronic Health Records
During EHR transfers, your stored data is more vulnerable to hacker attacks. The stored information can be easily copied by third parties, and it can be lost during the transferring process due to system fragility.
#4 Third-Party Data Access
This is another risk factor that can have a huge impact on the company’s image and the entire workflow. Hackers can benefit from it by disclosing or selling the clients’ data.
#5 Employee or User Errors
This risk factor refers to the internal app issues caused by bugs, wrong coding, unfriendly user interface design, etc. Additionally, a common reason for data vulnerability is that the patients often ignore the security of personal login credentials which can lead to account loss.
Employees’ errors can also result in disastrous and expensive consequences for a healthcare organization. Security awareness practice helps train healthcare workers in making rational decisions in critical situations.

Best Solutions for Ensuring Information Security in Healthcare Apps
Ironically, new technologies can also come to the rescue when you need to protect the patients’ and users’ data. Modern protection techniques can greatly improve your healthcare app and help it comply with all the relevant laws and regulations.
So, what are the major improvements you can apply to your healthcare app?
Two-Factor Authentication
To avoid third-parties intervention, it is generally advised to use two or more validation methods. Two-factor authentication is a great method that requires users to confirm their identity before they gain access to software. To enhance data safety, make sure to include information known only to the user, like the password or PIN number, and apply some specific keys, such as biometrics (facial recognition, fingerprints, etc).
Data Wiping
Leveraging big data requires huge storage capabilities. The more information you have to store, the more difficult it is to manage. Nevertheless, if you back up, archive the data, and dispose of the files you no longer need, you will save up resources and increase data security.
Continuous App Testing and Updates
Medical software requires continual improvements. Regular tests of the system for any bugs or vulnerabilities that should be fixed are essential for data protection. Furthermore, you will get the benefit of optimizing your app’s user experience (UX).
SSL Technology
By implementing the Secure Sockets Layer (SSL) protocols, a company can create a secure environment that can be used by the authorized staff only. Another benefit of this technology is that it can establish a secure encrypted connection by using public and private keys. That enhances the security of your server and helps to improve data security.
Backup
To prevent data loss caused by hacking attacks, it is suggested to make regular backups of all the data. Now, most hosting companies provide backup and recovery services, which are must-haves while leveraging big data. Storing the patients’ data in different places, can significantly reduce the number of data breaches and make the system less vulnerable.
Storage Encryption
All protected health information that you store should be encrypted in compliance with all the international regulations. Besides, this is a great option for limiting access to the authorized medical staff. And, if the server is compromised in any way, the data will be still encrypted and inaccessible for intruders.
Conclusion
Healthcare data security is one of the most critical issues you have to keep in mind while launching your own app in the medical industry. Firstly, it is an obligatory requirement of federal and international data protection regulations. Secondly, the data vulnerability can lead to business losses and will have a negative impact both on the company’s reputation and internal processes.
However, by applying novel yet proven technologies, you can prevent data breaches and other illegal activities around your patient PHI and otherwise improve your software and customer experience.
If you’re interested in a professional approach and secure app development, please contact us. The Onix team has real expertise in the health tech industry, can offer modern solutions that perfectly fit your healthcare software, and can resolve your most complicated problems.
Meanwhile, you may wish to download our checklist with tips on how to ensure your healthcare software security and data integrity. It may also prove handy when you decide to create your own app or need to make sure your developers are building a product suitable for a local or global market.
Content created by our partner, Onix-systems.
 Home
Home