Overview of Online Travel Fraud and Means of Its Prevention
Ecommerce presents tremendous opportunities for businesses and customers, but they go hand-in-hand with new threats. As technology advances, so do the methods of digital fraud. Payments that are made online in advance are particularly prone to attack.
Recent research from IBM showed that travel and transportation is the second-most targeted industry for online hackers. Fraudulent online activities cost the industry billions of dollars every year in direct losses, higher operating expenses, reputational damage, and other indirect costs.
Around 60% of travel intermediaries surveyed in a global study commissioned by eNett International in late 2017 recognized fraud as a major concern when making payments to suppliers. The three most-cited cases were stolen payment method details, cyber breach of online booking platforms, and stolen security credentials.
According to the Fraud Attack Index released by the ecommerce fraud prevention leader Forter in October 2019, fraud attack rates against airlines increased by 61% over the last year. This may be attributed to the rise in loyalty program issues and data hacks which made information of thousands of customers available for committing airline ticket frauds. Attacks against ground transportation have risen by 38%. The reason may be that car rentals and ride services have been removing some traditional barriers, such as proof of identity, from the customer journey.
Luckily, travel businesses can protect themselves with modern online fraud prevention tools without compromising the customer experience. Let’s examine some of the most common threats along with fraud management methods.
Common Types of Online Travel Fraud
The methods which fraudsters use for extorting money and valuable information from travelers and companies include, but are not limited to:
Booking with fake or stolen credit cards.
A fraud attack typically begins with obtaining consumers’ credit card numbers and identifying information. Identity theft was the third-most-common type of fraud in the United States in 2018, accounting for 15% of the nearly 3M fraud cases reported to the Federal Trade Commission. Criminals are stealing cardholders’ information through data breaches, card skimming, or malicious programs installed on legitimate websites. The numbers of credit cards and other data end up in the black market, where others buy them to perpetrate online purchase frauds.

Scammers buy tickets to resell on darknet marketplaces or even for cash in the open. Vendors scan the numbers and since the cardholders have not reported their cards as stolen, the numbers clear. Stolen credit cards form a volatile combination with last-minute booking because it leaves airlines, hotels, or online travel agencies (OTAs) less than 48 hours for possible fraud detection. Scammers would often buy a ticket the day before departure and promptly check in for the flight online. They know that even if OTA detects the fraud, the airline would hardly deny boarding to a confirmed passenger.
Fraudulent ticket cancellations.
Using stolen credit card data, scammers buy refundable tickets. Then, they call to cancel and cash in on the refunds. Particularly, they have been actively abusing ground transportation return policies, cashing in on stolen online train and bus tickets upon return at the stations. When fraudsters cancel airline tickets, they still earn the bonuses which they can resell or use to buy legitimate tickets.
Fake travel agencies.
Fraudsters create fake travel agencies, and then either purchase tickets or place holds on them with fake credentials. Travelers pay full prices for these fraudulent tickets only to find out that their airfare is fake or has been reported as fraudulent. When they try to seek reparation, the fake agency would not be there any longer.
Account TakeOver (ATO).
Account fraud is one of the fastest-growing and costliest threats for ecommerce. Knowing that people often use the same email and password combination for multiple accounts, hackers use databases of stolen credentials in attempts to log into a travel website. Otherwise, they may apply large volumes of data to ‘guess’ the right credentials via trial and error. Both methods are used to take over accounts and steal customer information or resources, e.g., loyalty points and miles.
When fraudsters are able to obtain complete user information, they typically try to impersonate that individual for online purchase frauds. If only partial information is available, they create synthetic accounts by combining data from multiple cardholders.
Modern travel agencies are dependent on global distribution systems. Amadeus, SABRE, and Travelport are ‘motherboards’ for hundreds of computerized reservation systems for airlines, hotels, and other vendors. Unfortunately, criminals can acquire a travel agent’s booking system login on the dark web as well. They are usually obtained through phishing: the agent receives an email, apparently from an online payment processor or another trusted source. The phisher asks for email login data or other essential information. If they succeed, they can monitor the agents’ email, looking for a chance to interfere in a transaction.

Insider fraud.
Besides having their username and password stolen, a travel agent may willingly hand them over to a swindler. The latter can then make fraudulent bookings using the agent’s credentials and stolen credit cards.
Fictitious hotels.
The hotel, villa or chalet exists only online. The swindler creates a simple website and uses a burner phone number that allows individuals to book rooms and pay over the phone. The swindler may also use stolen credit cards to book the rooms on an OTA’s website. The OTA will receive chargebacks for bookings after making a payment to the fake hotel. By this time, the swindler will have withdrawn the funds and will ignore all contact attempts.
Hotel price spike.
A collusion between a hotel and a fraudster using stolen credit cards may take place. The hotel would raise prices for its rooms, and the fraudster will book them through an OTA. The OTA becomes responsible for paying the chargebacks of the higher pricing. If they try to find out how the hotel booked non-existing people, the hotel would have all the false documentation.
Chargebacks / friendly fraud.
Online shoppers can deliberately abuse the chargeback process to get something for free. Hotel booking chargebacks are rampant, and they can affect travel intermediaries as well. For example, a customer purchases an expensive vacation package through a travel agency, but even one aspect of the experience can make them demand a chargeback on the entire vacation.
In some cases, purchases are made with the intent to file a chargeback later. The fraudster would take a flight and deny it when the airfare appears on a credit card bill. They may persuade the card issuer to cancel the transaction, and since not every OTA will fight back, it would have to pay the bill for the flight.
Cyber breach.
Any tourism-related company that processes large quantities of customer data can be the target of an attempted breach. It can damage the company’s reputation and leave it open to possible legal action.
Malicious bot attacks.
The increasingly sophisticated and frequent bot attacks on travel sites are intended to access sensitive customer data or to give an advantage to dishonest competitors.
For example, unscrupulous entrepreneurs may send bots to scrape pricing on competitor sites. Then they would automatically update their own website to show a lower price. Scalping bots buy up the entire supply of an offer on site to resell it at a higher price. Seat spinning bots hold or block multiple airline reservations without paying for them to prevent legitimate customers from doing so. Scraping bots can also copy a website’s entire contents to resell or reuse them for fraudulent purposes.
New tricks and techniques emerge regularly, and travel businesses are responding by developing new fraud protection methods and adopting new instruments.
Online Fraud Prevention Tools and Best Practices in the Travel Industry
Monitoring of transactions and fraud scoring
Every transaction is examined for multiple fraud indicators, generating a composite score as a level of risk that the transaction represents. At checkout, companies focus on:
- Type of credit card. According to the study sponsored by eNett, 29% of travel intermediaries identified foreign credit cards as the highest fraud risk when receiving payments. Fraudsters also tend to prefer certain credit cards to others.
- Geolocation. If there is a mismatch between the user’s IP address and billing information, it could suggest fraud.
- Transaction velocity. Fraud detection tools are watching for repeated purchases from the same user. Fraudsters usually try to run-through as many sales as possible before they are exposed, so a hike in purchases from one cardholder is a red flag.
Combined with user verification, fraud scoring tools enable companies to reject transactions that raise too many red flags automatically.
Order rescreening is important too: all order modifications should be monitored and evaluated for fraud.
User profiling
Getting a complete customer profile helps businesses avoid much trouble. OTAs and other companies garner tons of data from their customers and transactions, including:
- identity information, such as the customer’s credit cards, email address, and social networks;
- behavioral data on what the customer does on the website or mobile application;
- user’s connections via devices, email, address, or location.
User verification is done through:
- User identity verification. To handle ATO or synthetic account fraud, companies are seeking authorization for a transaction before providing services, using Address Verification Service (AVS), verifying the card security code (CVV or CVC), and recognizing photos of identity documents online. AVS-based fraud prevention tools match the billing address provided by a customer with the address on file with the card issuer. A mismatched billing address may suggest fraud. A mismatch between the user’s geolocation tag and the billing information on file may be a sign of ATO. As for CVV/CVC, legitimate cardholders usually either remember the 3- or 4-digit codes printed on their credit cards or have the card at hand to provide the code. Verification through scanned ID, such as a passport or a driver’s license, adds another layer of security to every online transaction. There are software-as-a-service (SaaS) products that include passport and customized ID verification, and more. The wealth of user identity records and cooperation between human intelligence and Artificial Intelligence (AI) within the SaaS architecture allow to verify 7 Billion people with 99.6% precision.
- IP address analysis. When a person places an order, geolocation technology pinpoints them based on the IP address associated with the order. Comparing the location against the information on file with the card issuer allows verifying whether the request was submitted from a reasonable location. IP address analysis also helps reveal whether a proxy, virtual private network, or Tor browser is used to enable anonymous communication. When scammers use proxies, it’s harder to trace their location, but proxy piercing may help.
- Email address analysis. Email addresses can reveal a lot about a user, e.g., whether it is from a high-risk domain or was used to register social media accounts. Nowadays, users without any social media presence have a 90% chance of being fraudsters.
- Device fingerprinting. This method identifies purchases made through a particular device using the unique information left by the hardware and software installed on it. Using device fingerprinting, firms become able to block devices previously associated with fraudulent activity.
- Blacklists and whitelists. It’s possible to filter individuals and entities to deal with. A ‘blacklist’ allows blocking specific users or users sharing a definite trait. A ‘whitelist’ will eliminate all traffic that doesn’t meet the defined parameters.
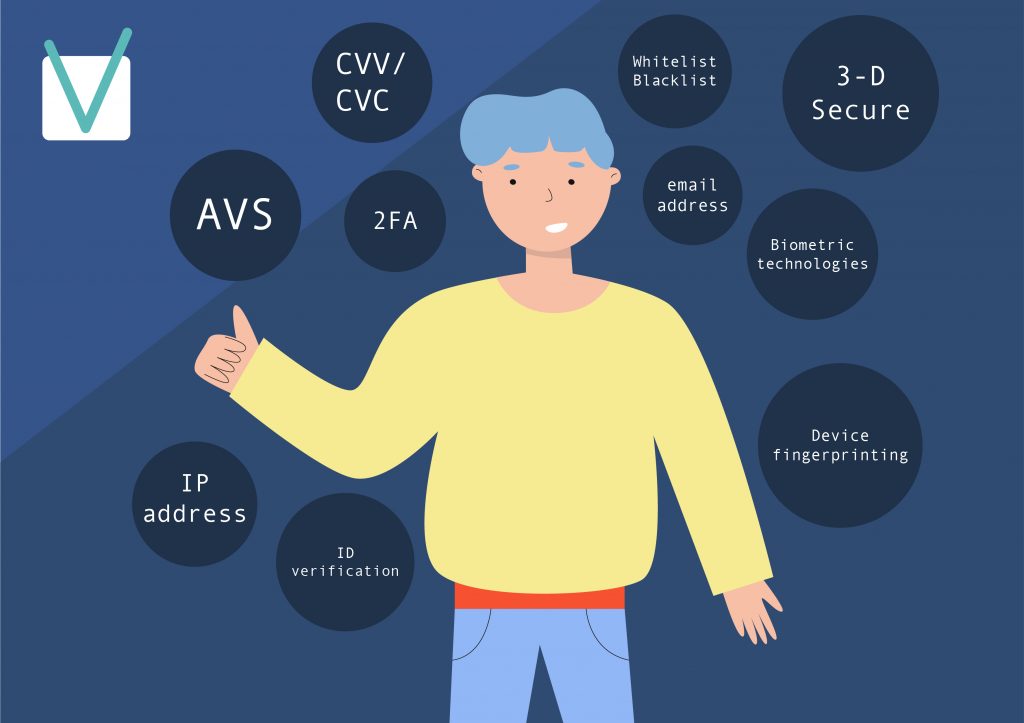
Anti-ATO mechanisms
- 3-D Secure works as an online PIN code. At checkout, it directs users to a separate page to enter a unique code. This adds insignificant friction for legitimate customers but places a barrier in front of swindlers.
- Simple two-factor authentication also helps prevent travel agent ATO. When authorized employees log into the travel agency’s booking platform, they receive a verification request on their mobile phone. This prevents criminals from accessing the system.
- Biometric technology and mobile payments can significantly support a company’s anti-fraud strategy. Mobile wallet apps like Apple Pay and Google Pay rely on two-factor authentication. The user needs to unlock the device with a passcode or thumbprint and then enter a secondary ID to authorize a purchase. Moreover, the transactions are tokenized for additional data security.
Supplier verification
Double-checking the suppliers before making payments helps mitigate the fake hotels problem. OTAs need to check their business license, online Google Business reviews, or just see the Google Street View of the supposed hotel location. It’s also important to check for a possible correlation between increases in hotel prices and booking activity, which may indicate hotel price spike scam.
Data breach prevention methods
- Consistent compliance with the Payment Card Industry Data Security Standard;
- disposing of digital data and hard copies in a secure manner;
- regular training of employees in best practices of data security, including strong password conventions;
- strict control of access to all computers and private networks;
- staying abreast of new security developments and technologies.
Machine learning solutions
Modern online fraud detection is primarily about pattern recognition, so machine learning (ML) becomes the backbone of fraud protection strategies. ML models learn to recognize patterns and predict outcomes. The method may help highlight behavior anomalies in real time, flag an ATO risk, help evaluate the transaction’s riskiness, and block it before it becomes a chargeback.
Within milliseconds between an online transaction and an automated decision, a fraud prevention system adds to each transaction record countless elements of data: all transactions and results associated with the transaction’s IP, email address, physical address, device, products purchased, number of tickets in the transaction, distance from purchase location to departure airport, the time between purchase and check-in and departure, and other travel-related data elements. This way, ML algorithms can identify thousands of signals for hundreds of fraud schemes and attack vectors, including inside fraud. For example, multiple departure/destination airport pairings are suspicious. ML algorithms also score the transactions based on learnings from other frauds. Transactions that raise certain combinations of red flags can be rejected outright or set aside for manual review.
The more data the company has, the better the algorithms will be detecting fraud signs. Over time, their speed and accuracy will be growing, and they will be learning to detect new signals to keep pace with new travel scams. Since companies find out scammers after the fact through bank account reconciliations, chargebacks, or empty seats, continuous feedback is essential. It’s beneficial to share databases with multiple travel agencies, airlines, and other travel firms. Once a network member identifies fraud, the perpetrator’s digital identity and history become available to all. More online and call center transactions, with more logged results from more companies, will generate more accurate fraud decisions.
Machine learning is beneficial for sales growth as well. Some airlines reportedly reject up to 25% of legitimate orders suspecting fraud. A good fraud prevention tool will pass a higher percentage of safe transactions.
Measures against malicious bots
Usually, companies notice bad bot activity due to abnormal spikes in traffic on their websites and apps, or when the amount of traffic during peak times is higher than expected. To curb illegitimate traffic, some implement infrastructure-level protections or, if the traffic levels are low, manual bot filtering. However, it is very resource-consuming. Real-time protection against bots requires an integration of various methods, such as:
- Comparing every website request against the in-memory pattern database.
- Using AI and ML to identify and block bots quickly.
- Networking that enables automatic protection of all members within milliseconds after a new bad bot is detected on any of the protected domains.
Friendly fraud management
Unfortunately, it’s impossible to prevent chargeback abuse. The only response is to fight back through chargeback representment. OTAs need to submit compelling evidence to prove the transaction was legitimate and should be upheld, including:
- Order forms, especially those outlining special requests
- Tracking numbers
- OTA-customer communications logs
- Evidence that the cardholder has used the travel product (social media posts, photos, etc.)
- Confirmation for items delivered to an address matched with AVS
Summing Up
Online fraud is rampant in the tourism and travel industry. Manual review queues are not efficient enough to keep up with the growing online business. The cost of falsely declined transactions may exceed the total cost of fraud. As online fraudsters are shifting their efforts earlier in the customer journey, travel businesses need to respond by implementing a continuous fraud prevention approach that automatically assesses events and provides protection throughout the entire customer journey.

Travel businesses have been innovators and investors in pre- and post-transaction anomaly detection and risk-scoring. There are instruments that increase the efficiency of manual review teams and entire SaaS fraud detection platforms that can stop suspicious transactions at the booking request stage, flag them, and even cancel. With best practices in place, companies can also learn how to avoid disputes caused by merchant error and criminal fraud. However, innovative enterprises turn to fraud prevention solutions that combine technological advances to detect payment fraud, account takeover, phishing, and other threats across thousands of transactions in real time. Careful data analysis enables smarter fraud prevention, and machine learning algorithms applied to transactions not only recognize legitimate and fraudulent transactions but also reveal trends and developing threats. Systems that incorporate ML models and AI are equipped to deal with massive amounts of data and to improve overall decision results over time.
Fraud management mechanisms and a secure digital infrastructure are vital components of modern business management, and only coordinated, carefully planned adoption of different tools allows addressing online travel fraud effectively. A data-informed, multilayer approach helps to prevent fraud attacks without increasing false declines. Besides fraud reduction, an effective platform minimizes the number of transactions reviewed and the time required for each review. Automated fraud prevention does not add any friction to the customer experience regardless of the season. As AI and ML tools are evolving, companies are increasingly capable of reducing manual reviews and increasing margins. The integration of such solutions also facilitates simplified reconciliation, reduced risk of supplier default, and accelerated payment processes. It frees travel companies from infrastructure resource waste and lets them concentrate on business growth.
Content created by our partner, Onix-systems.
 Home
Home