SaaS Application Security – Alternative-spaces’ Guide for Startups

Back in 2019, 94% of enterprises were reported to be using cloud computing, including software as a service (SaaS) applications. Remote work and virtual setup have further proliferated this model.
The need for increased SaaS application security grows in sync with the increasing demand for SaaS services and attackers becoming more sophisticated. The number of threats targeting cloud services in 2020 increased by an astounding 630%.
SaaS security concerns are one of the main hurdles in adopting cloud solutions, especially by small and medium-sized companies. They may doubt an app’s regulatory compliance or cloud application security in general, whereas such apps often store consumers’ credit cards and other sensitive information.
Breach detection and mitigation may be the least of SaaS business owners’ worries. It may take months to recover from damage caused by a cyberattack. If it results in the loss of sensitive information, the damaged reputation and legal and financial implications can be detrimental even for an established company. Increased customer churn and customer acquisition cost may finish a startup.
SaaS applications are mostly built using cloud platform services (PaaS), deployed on cloud infrastructure (IaaS), and hosted and managed by several providers. Their security is developed at all layers but owned mainly by the service provider.
If you are interested in SaaS cloud security, the OWASP‘s cloud top 10 risks provide a good starting point. This article focuses on the basic steps every SaaS business owner can take to secure their application.
In the following chapter, you can find an outline of major SaaS security issues to address during your software development process. The second chapter offers practical tips to enhance the security of your SaaS applications.
The Common SaaS Security Issues
It’s helpful to look at potential vulnerabilities, threats, and risks well before beginning your product development. It’s easier and cheaper to build a secure application from the ground up than eventually dealing with SaaS security breaches.
Some of the critical risks to SaaS data security include, but are not limited to:
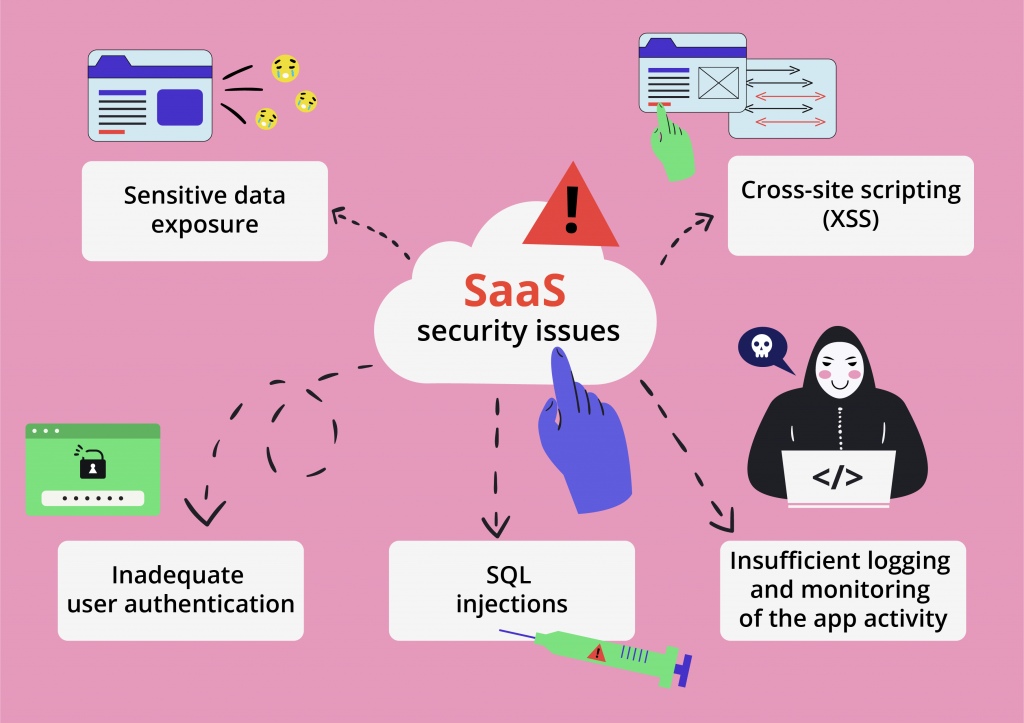
- Sensitive data exposure
Cybercriminals can steal weakly protected sensitive data, such as personally identifiable information, social security numbers, credit card information, etc., and use them for identity theft, fraud, and other illicit activities.
Software developers undermine defenses and enable attacks by using components with known vulnerabilities, incorrect setup of computing assets, or overlooking errors in the operating system, middleware, or database.
For example, a preserved default account with the original password leaves the web app vulnerable to attacks.
- Cross-site scripting (XSS)
Hackers can use a SaaS app’s code flaws to inject malicious code (scripts) into a web page viewed by a user. It gives them access to the user’s browser and lets them hijack user sessions and redirect users to malicious sites.
- Inadequate user authentication
Flawed authentication and session management functions in many SaaS products give bad guys opportunities to compromise passwords, session tokens, or keys and steal users’ identities.
Notably, a popular online credit card payment method may pose the risk of identity theft. Inadequate enforcement of access restrictions enables cybercriminals to operate as administrators or authenticated users, modify access rights and user information, and view files.
- SQL injections
Structured Query Language (SQL) is a programming language used to maintain most databases. By inserting specialized SQL statements into an entry field, an attacker makes the system execute commands that allow various manipulative behaviors.
For example, the security risks of multi-tenancy architecture include injecting a tenant and trying to cross the boundary of another tenant to access their restricted data.
Attackers can emulate the identity of a more privileged user, make themselves or others database administrators, tamper with, retrieve, or destroy all server data, modify transactions and balances, and even gain complete control over the system.
- Insufficient logging and monitoring of the app activity
Without proper frequent logging and monitoring, you risk overlooking unauthorized and potentially malicious activities, such as tampering, theft, or destruction of data, indirectly encouraging and facilitating the attackers’ efforts.
Continuous risks and app security assessment should be integral to your product development process. The understanding of vulnerabilities will enable the team to face the most common security problems, protect the vulnerable hotspots, develop practices to minimize risks, and devise protection from emerging cyber threats.
Your software development team also has to be committed to implementing SaaS security best practices from the onset. Let us recommend a few.
SaaS Security Best Practices

Develop a detailed SaaS security requirements checklist
This checklist should include the potential security flaws to watch out for, established SaaS security standards, and internal measures promoting security.
The regulations and standards you may have to follow may include, but are not limited to:
- General Data Protection Regulations (GDPR) if you are going to provide services in the European Union and the European Economic Area.
- Payment Card Industry Data Security Standard (PCI DSS), which applies to all entities that collect, transmit, or store credit card information.
- Health Insurance Portability and Accountability Act (HIPAA), if you are going to store and transmit patients’ data between devices.
- the Health Information Technology for Economic and Clinical Health (HITECH) Act, which also applies to medical apps in the US.
- ISO/IEC 27001, an international certificate that fintech entities may be required to implement.
- Sarbanes–Oxley Act (SOX), a US federal law that mandates certain practices in financial record keeping and reporting.
- NIST 800-171, a special publication by the National Institute of Standards and Technology that recommends requirements for protecting controlled unclassified information by defense contractors.
- The Center for Internet Security (CIS) best practices.
On the organizational level, SaaS security can be promoted by:
- public and internal security policies
- regular information of the employees about the security measures you expect them to follow
- cybersecurity training for employees to help prevent social engineering, phishing, and other hacker attacks
- usage of password managers
- centralized user management that controls the dataflow within your app ecosystem
- information of your customers about the data you collect and process
- customer education aimed at preventing account takeover fraud and other attacks
Brainstorm within your software developers, stakeholders, and domain experts to curate a SaaS security checklist that best suits your startup’s needs. An expert agency like Alternative-spaces can help you define the key checkpoints and offer actionable advice on protecting your SaaS application and customers.
Regularly review and update your checklist and make it easily accessible to keep all involved on the same page throughout your product development and keep abreast with current security threats and developments.
Ensure a Secure Software Development Life Cycle
Secure SDLC implies activities promoting security at every stage of a product’s life cycle so that security is baked into the process. These may include integrating SaaS application security requirements alongside functional requirements in your project specification, analyzing architecture risks during the discovery phase, technology choice, adopting secure coding methodologies, penetration testing, and other measures.
These activities should enable you to detect and eliminate potential vulnerabilities or weaknesses as early as possible. For instance, using the latest versions of libraries and frameworks can automatically prevent XSS.
It is a good idea to introduce DevOps security early in the SaaS product life cycle. Among other benefits, it helps reduce data breaches.
Implementing a CI/CD pipeline facilitates rapid delivery of features and fixes, including security-related. The process of building an application or feature, integrating it, and finally deploying prevents errors from causing damage before they are deployed. Easy identification of the source enables immediate fixing of any errors.
Perform proper SaaS application security testing
Besides the standard quality assurance and automated testing, your SaaS product development should include security-specific testing. For example, you can use a static application security testing (SAST) tool to analyze your application source code and highlight the security vulnerabilities, if any. The OWASP Testing Guide includes information about security monitoring and various test procedures.
The whole technical team can participate in simulated attacks on the product’s weak spots in search of vulnerabilities.A full blind discovery will facilitate a more profound audit of your SaaS platform. Outsider professional penetration testers question even basic assumptions and provide a comprehensive list of vulnerabilities and issues to address urgently.
Perform proper SaaS application security testing
SaaS business owners may need to obtain certifications like PCI DSS to prove that sensitive data is transmitted, processed, and stored securely. For instance, a SOC 2 audit aims to assess a service organization’s security, processing integrity, and confidentiality and privacy controls based on its compliance with the Trust Services Criteria of the American Institute of Certified Public Accountants.
These essential certifications are something customers look for when selecting a SaaS vendor, a good indicator of a vendor’s readiness for regulatory compliance and maintaining high data security standards.
Data retention policies are often a major compliance requirement. The law may require that some data, e.g., names, addresses, social security numbers, and financial records, be retained for a specific period and deleted when you no longer need it. Other data might be important to your business but not necessarily require retention.
SaaS businesses need to have a data retention policy for their applications, especially for account management and subscriptions. A data deletion policy must specify what would happen to the customer data once the data retention period ends: the data should be deleted programmatically from your systems. A data deletion process needs to be implemented accurately and on time, with relevant logs being generated and maintained.
Integrate real-time protection
Real-time monitoring can help the system distinguish between legitimate queries and malicious attacks, such as SQL injections, XSS, and account takeovers. Real-time protection tools, such as protection logic, can be integrated into the code at the development stage.
The integration of real-time monitoring into your SaaS app results in improved visibility, compliance, control, and policy management. After launch, you can integrate third-party security services.
Ensure secure SaaS application deployment
Two main options are available for SaaS deployment:
1. Self-hosted deployment. In this scenario, it will be your responsibility to thoroughly research SaaS security issues, adopt stringent application security policies, and implement appropriate safeguards to prevent denial-of-service (DoS) and network penetration attacks. Best practices for solving this problem include continuous integration, delivery, and deployment. It is also recommended to automate the deployment process as much as possible.
2. Cloud deployment. Public cloud vendors like Amazon or Google take a shared responsibility of securing SaaS applications. Their infrastructure services help ensure data segregation, data security, network security, etc. If you choose to deploy your SaaS app on a public cloud, make sure to adhere to the best practices and norms recommended by the vendor. It’s also a good idea to check the service’s compliance with applicable security principles and standards.
Implement data encryption
Encryption lets you protect data against unauthorized users by encoding it. Even if they manage to break through security barriers, they won’t be able to use your data without the encryption keys which only authorized users have.
Secure encryption configuration provides the needed protection from eavesdropping, tampering, or other interferences with data in transit between the clients and service vendors. All of the app’s interactions with the servers should occur over the Transport Layer Security protocol to ensure encryption during transmission. TLS 1.2 is the most popular version currently. The certificates used for protecting the external data should be correctly configured and follow good practices. The TLS should only terminate within the cloud service provider.
Sensitive data in transit between microservices, whether within the same cloud or multiple cloud services, must be protected at the same levels as client/service data transfers.
Data in storage should also be encrypted to protect sensitive information. Cloud service providers often provide field-level encryption and allow their customers to specify the fields they want to encrypt, such as credit card numbers.
Data at rest may utilize strong cloud security measures for backup data, similar to your laptop’s hard drive data encryption. Datastores in a SaaS database must be classified and encrypted to the level of user needs. Data in lower SaaS environments has to be equally secured.
Use proven cryptography tools
Your software development team should use the best cryptography libraries, mechanisms, and tools, such as:
- authentication token
- authentication using keys
- JCA, cryptographic libraries in Java
- Docker, which keeps the files and data inside the containers in encrypted form
- CertMgr.exe and SignTool.exe
SaaS Security Checklist for Your Startup
We hope that this article proves helpful. For your convenience, we have also curated a list of recommendations where every organization can find relevant SaaS security best practices or base its unique checklist on the template.
If you have questions about SaaS application security, please feel free to contact Alternative-spaces. Our award-winning web and mobile app development agency has vast experience in developing secure SaaS applications. We provide our outsourcing clients with senior tech talent and product development expertise, and deliver quality solutions on time and within budget. We can help you develop your startup’s security strategy or build a product with impenetrable SaaS security from A to Z.
Let’s talk about your SaaS project needs today!
Content created by our partner, Onix-systems
 Home
Home